й—®йўҳиғҢжҷҜпјҡ
и®ҫеӨҮпјҡIPC CameraпјҢе…¶wifiж”ҜжҢҒ80211.bgnеҚҸи®®пјҢж”ҜжҢҒWPAпјҢWPA2е®үе…ЁеҚҸи®®гҖӮ и·Ҝз”ұеҷЁпјҡ2.4Gе’Ң5GеҸҢйў‘WIFIпјҢж”ҜжҢҒWPA+WPA2пјҢWPA2, WPA2+WPA3е®үе…ЁеҚҸи®®гҖӮ
~ # wpa_cli -i wlan0wpa_cli v2.9Copyright (c) 2004-2019, Jouni Malinen <j@w1.fi> and contributorsInteractive mode<3>CTRL-EVENT-SCAN-STARTED<3>CTRL-EVENT-SCAN-RESULTS<3>CTRL-EVENT-SSID-REENABLED id=0 ssid="your-ssid"<3>SME: Trying to authenticate with 2c:3a:fd:2c:fa:97 (SSID='your-ssid' freq=2437 MHz)<3>Trying to associate with 2c:3a:fd:2c:fa:97 (SSID='your-ssid' freq=2437 MHz)<3>Associated with 2c:3a:fd:2c:fa:97<3>CTRL-EVENT-SUBNET-STATUS-UPDATE status=0<4>WPA: Failed to configure IGTK to the driver # еҸҜд»ҘзңӢеҲ°жӯӨеӨ„жҳҜеңЁй…ҚзҪ®IGTKж—¶жҠҘй”ҷпјҢ<3>RSN: Failed to configure IGTK # еҸҜд»ҘзңӢеҲ°жӯӨеӨ„жҳҜеңЁй…ҚзҪ®IGTKж—¶жҠҘй”ҷпјҢ<3>CTRL-EVENT-DISCONNECTED bssid=2c:3a:fd:2c:fa:97 reason=1 locally_generated=1<3>CTRL-EVENT-SSID-TEMP-DISABLED id=0 ssid="your-ssid" auth_failures=3 duration=46 reason=CONN_FAILED<3>CTRL-EVENT-SCAN-STARTED<3>CTRL-EVENT-SCAN-RESULTS
еҲҶжһҗжӯҘйӘӨпјҡ
ж №жҚ®logжҠҘй”ҷдҝЎжҒҜеҸҜзҹҘпјҢwifiзҡ„и®ӨиҜҒпјҲauthenticate пјүе’Ңе…іиҒ”пјҲassociatedпјүжӯҘйӘӨйғҪжҳҜжҲҗеҠҹзҡ„пјҢи®ҫзҪ®IGTKжӯҘйӘӨеӨұиҙҘдәҶгҖӮзҷҫеәҰдёҖдёӢIGTKжҳҜдёӘд»Җд№ҲдёңиҘҝгҖӮ
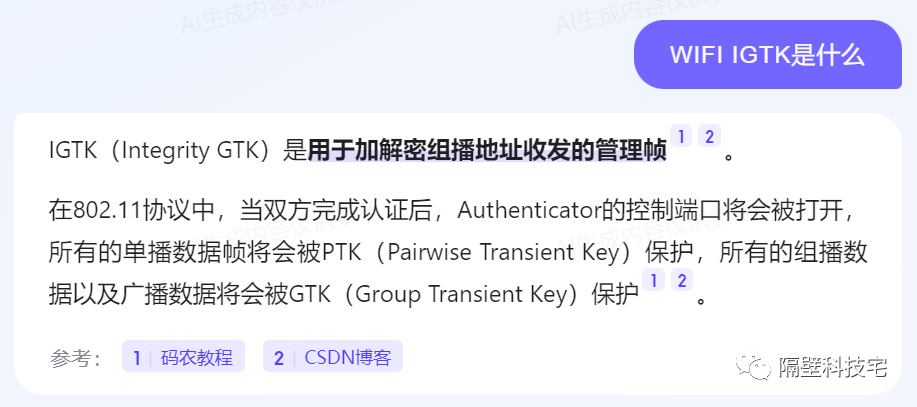
IGTKд№ҹе°ұжҳҜз®ЎзҗҶеё§еҠ еҜҶзӯ–з•ҘпјҢйӮЈдёҚе°ұжҳҜieee80211wеҚҸи®®ж”ҜжҢҒзҡ„mfpпјҲManagement Frame ProtectionпјүеҠҹиғҪеҳӣпјҢеӣ дёәи®ҫеӨҮдёӯжҳҜеә”з”ЁйҖҡиҝҮwpa_cliе·Ҙе…·иҝӣиЎҢй…ҚзҪ‘зҡ„пјҢжүҖд»Ҙ/etc/wpa_supplicant.confж–Ү件дёӯжІЎжңүе…·дҪ“зҪ‘з»ңдҝЎжҒҜпјҢдҪҝз”Ёsave_configе‘Ҫд»ӨеҜјеҮәй…ҚзҪ®иҝӣиЎҢзЎ®и®ӨгҖӮ
> save_configOK>q~ # cat /etc/wpa_supplicant.confctrl_interface=/var/run/wpa_supplicantupdate_config=1network={ssid="your-ssid"scan_ssid=1psk="your-psk"key_mgmt=WPA-PSK WPA-EAP IEEE8021X WPA-PSK-SHA256 WPA-EAP-SHA256ieee80211w=1 # иҝҷйҮҢи®ҫзҪ®дёә1пјҢејҖеҗҜдәҶmfpеҠҹиғҪ}
жһң然пјҢnetworkдёӯй…ҚзҪ®дәҶieee80211w=1пјҢи®ҫеӨҮејҖеҗҜдәҶmfpеҠҹиғҪгҖӮеӣ дёәи·Ҝз”ұеҷЁж”ҜжҢҒWPA3пјҢжүҖд»Ҙи·Ҝз”ұеҷЁиӮҜе®ҡж”ҜжҢҒmfpпјҲWPA3йңҖиҰҒејәеҲ¶ејҖеҗҜmfpпјҢWPA2еҸҜйҖүжӢ©жҳҜеҗҰејҖеҗҜпјүпјҢ йӮЈе°ұжҳҜеҸҜиғҪжҳҜи®ҫеӨҮдёҚж”ҜжҢҒmfpгҖӮе°қиҜ•е…іжҺүieee80211wиҜ•дёҖдёӢгҖӮ
> set_network 0 ieee80211w 0OK> reconnectOK<3>CTRL-EVENT-SCAN-STARTED<3>CTRL-EVENT-SCAN-RESULTS<3>CTRL-EVENT-SSID-REENABLED id=0 ssid="your-ssid"<3>SME: Trying to authenticate with 2c:3a:fd:2c:fa:97 (SSID='your-ssid' freq=2412 MHz)<3>Trying to associate with 2c:3a:fd:2c:fa:97 (SSID='your-ssid' freq=2412 MHz)<3>Associated with 2c:3a:fd:2c:fa:97<3>CTRL-EVENT-SUBNET-STATUS-UPDATE status=0<3>WPA: Key negotiation completed with 2c:3a:fd:2c:fa:97 [PTK=CCMP GTK=CCMP]<3>CTRL-EVENT-CONNECTED - Connection to 2c:3a:fd:2c:fa:97 completed [id=0 id_str=]<3>WPA: Group rekeying completed with 2c:3a:fd:2c:fa:97 [GTK=CCMP]
жһң然пјҢе…іжҺүmfpеҗҺи®ҫеӨҮе°ұиғҪеӨҹжӯЈеёёиҒ”зҪ‘дәҶпјҢйӮЈе°ұиҜҒжҳҺзЎ®е®һжҳҜеӣ дёәи®ҫеӨҮдёҚж”ҜжҢҒmfpгҖӮжүҖд»ҘжңҖз»Ҳи§ЈеҶіж–№жЎҲе°ұжҳҜеҺ»жҺүieee80211w=1пјҹВ
NONONOпјҢеҗҢдёҖдёӘе№іеҸ°еҸҜиғҪдјҡжҗӯй…ҚдёҚеҗҢзҡ„WIFIжЁЎз»„пјҢ并дёҚжҳҜжүҖжңүжЁЎз»„йғҪдёҚж”ҜжҢҒmfpпјҢеңЁе…Ғи®ёзҡ„жғ…еҶөдёӢпјҢжҲ‘们иҝҳжҳҜйңҖиҰҒејҖеҗҜиҜҘеҠҹиғҪзҡ„пјҢжҜ•з«ҹиғҪеӨҹжҸҗдҫӣжӣҙејәзҡ„е®үе…ЁжҖ§гҖӮжүҖд»ҘжҲ‘们йңҖиҰҒжғіеҠһжі•и®©еҗҢдёҖеҘ—й…ҚзҪ®е…је®№дёӨз§ҚдёҚеҗҢеңәжҷҜпјҢдҝқиҜҒдёҚж”ҜжҢҒmfpзҡ„и®ҫеӨҮиғҪеӨҹжӯЈеёёиҒ”зҪ‘пјҢж”ҜжҢҒmfpзҡ„и®ҫеӨҮејҖеҗҜиҜҘеҠҹиғҪгҖӮ
е…Ҳй—®й—®зҷҫеәҰеҗ§пјҡ
зҷҫеәҰAIзңҹзүӣйҖје•ҠпјҢиҖҒй“Ғ666, ж”№дёҖжҠҠиҜ•иҜ•гҖӮ
~ # vi /etc/wpa_supplicant.confctrl_interface=/var/run/wpa_supplicantupdate_config=1network={ssid="your-ssid"scan_ssid=1psk="your-psk"key_mgmt=WPA-PSK WPA-EAP IEEE8021X WPA-PSK-SHA256 WPA-EAP-SHA256mfp=no}
жөӢиҜ•дёҖжҠҠ
~ # wpa_cli -i wlan0Interactive mode> reconfigureFAIL<5>Failed to parse the configuration file '/etc/wpa_supplicant.conf' - exiting> >
What fuck? wpa_supplicantеҺӢж №дёҚи®ӨиҝҷдёӘеҸӮж•°пјҢзҷҫеәҰдҪ TMеңЁйҖ—жҲ‘еҗ—пјҹ
з®—дәҶз®—дәҶпјҢиҝҳжҳҜйҮҚж–°зј–иҜ‘дёӘеёҰdebugж—Ҙеҝ—зҡ„wpa_suplicantеҗ§гҖӮжҚўз”ЁеёҰdebugж—Ҙеҝ—зҡ„wpa_supplicantд№ӢеҗҺпјҢеҲҶеҲ«е°Ҷи·Ҝз”ұеҷЁи®ҫзҪ®еҲ°WPA2жЁЎејҸе’ҢWPA2+WPA3е…је®№жЁЎејҸпјҢеҜ№жҜ”logзңӢеҲ°еҰӮдёӢе·®ејӮгҖӮ
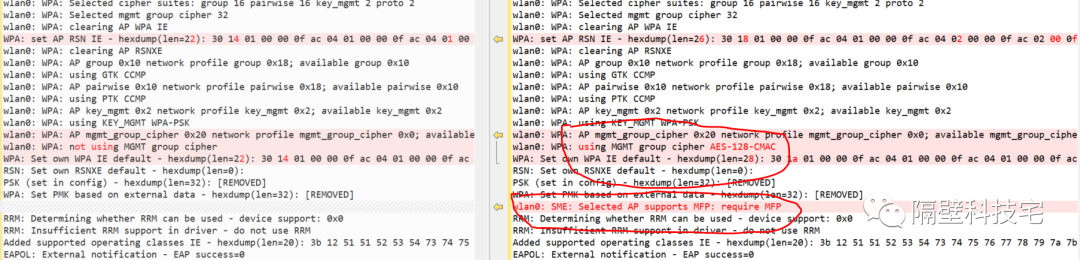
е…ій”®е·®ејӮеҰӮдёӢпјҡ
#В WPA2жЁЎејҸдёӢ,В еҚҸе•Ҷзҡ„з»“жһңmgmt_group_cipher=0x0пјҢиЎЁзӨәдёҚеҗҜз”Ёmfpwlan0: WPA: AP mgmt_group_cipher 0x20 network profile mgmt_group_cipher 0x0; available mgmt_group_cipher 0x0wlan0: WPA: not using MGMT group cipherWPA: Set own WPA IE default - hexdump(len=22): 30 14 01 00 00 0f ac 04 01 00 00 0f ac 04 01 00 00 0f ac 02 80 00RSN: Set own RSNXE default - hexdump(len=0):PSK (set in config) - hexdump(len=32): [REMOVED]WPA: Set PMK based on external data - hexdump(len=32): [REMOVED]#В WPA2+WPA3жЁЎејҸдёӢ,еҚҸе•Ҷзҡ„з»“жһңmgmt_group_cipher=0x20пјҢиЎЁзӨәеҗҜз”Ёmfpwlan0: WPA: AP mgmt_group_cipher 0x20 network profile mgmt_group_cipher 0x0; available mgmt_group_cipher 0x20wlan0: WPA: using MGMT group cipher AES-128-CMACWPA: Set own WPA IE default - hexdump(len=28): 30 1a 01 00 00 0f ac 04 01 00 00 0f ac 04 01 00 00 0f ac 02 80 00 00 00 00 0f ac 06RSN: Set own RSNXE default - hexdump(len=0):PSK (set in config) - hexdump(len=32): [REMOVED]WPA: Set PMK based on external data - hexdump(len=32): [REMOVED]wlan0: SME: Selected AP supports MFP: require MFP
дёҚеҗҢжЁЎејҸдёӢпјҢеҚҸе•Ҷзҡ„mfpзҠ¶жҖҒдёҚдёҖж ·пјҢWPA2+WPA3жЁЎејҸдёӢејҖеҗҜдәҶmfpеҠҹиғҪгҖӮжәҗз Ғдёӯжҗңзҙўжү“еҚ°вҖңAP mgmt_group_cipher 0x20 network profileвҖқжүҫеҲ°еҜ№еә”еҮҪж•°дҪҚзҪ®пјҡ
root@pc:~/hostap_2_10/wpa_supplicant$ grep -rn "WPA: AP mgmt_group_cipher" .Binary file ./wpa_supplicant matches./wpa_supplicant.c:1312: "WPA: AP mgmt_group_cipher 0x%x network profile mgmt_group_cipher 0x%x; available mgmt_group_cipher 0x%x",./events.c:2857: "WPA: AP mgmt_group_cipher 0x%x network mgmt_group_cipher 0x%x; available mgmt_group_cipher 0x%x",
жү“ејҖwpa_supplicant.cзҡ„1312иЎҢпјҢеҰӮдёӢпјҡ
void wpas_set_mgmt_group_cipher(struct wpa_supplicant *wpa_s,struct wpa_ssid *ssid, struct wpa_ie_data *ie){int sel;sel = ie->mgmt_group_cipher;if (ssid->group_mgmt_cipher)sel &= ssid->group_mgmt_cipher;if (wpas_get_ssid_pmf(wpa_s, ssid) == NO_MGMT_FRAME_PROTECTION ||!(ie->capabilities & WPA_CAPABILITY_MFPC))sel = 0;wpa_dbg(wpa_s, MSG_DEBUG,"WPA: AP mgmt_group_cipher 0x%x network profile mgmt_group_cipher 0x%x; available mgmt_group_cipher 0x%x",ie->mgmt_group_cipher, ssid->group_mgmt_cipher, sel);if (sel & WPA_CIPHER_AES_128_CMAC) {wpa_s->mgmt_group_cipher = WPA_CIPHER_AES_128_CMAC;wpa_dbg(wpa_s, MSG_DEBUG,"WPA: using MGMT group cipher AES-128-CMAC");} else if (sel & WPA_CIPHER_BIP_GMAC_128) {wpa_s->mgmt_group_cipher = WPA_CIPHER_BIP_GMAC_128;wpa_dbg(wpa_s, MSG_DEBUG,"WPA: using MGMT group cipher BIP-GMAC-128");} else if (sel & WPA_CIPHER_BIP_GMAC_256) {wpa_s->mgmt_group_cipher = WPA_CIPHER_BIP_GMAC_256;wpa_dbg(wpa_s, MSG_DEBUG,"WPA: using MGMT group cipher BIP-GMAC-256");} else if (sel & WPA_CIPHER_BIP_CMAC_256) {wpa_s->mgmt_group_cipher = WPA_CIPHER_BIP_CMAC_256;wpa_dbg(wpa_s, MSG_DEBUG,"WPA: using MGMT group cipher BIP-CMAC-256");} else {wpa_s->mgmt_group_cipher = 0;wpa_dbg(wpa_s, MSG_DEBUG, "WPA: not using MGMT group cipher");}wpa_sm_set_param(wpa_s->wpa, WPA_PARAM_MGMT_GROUP,wpa_s->mgmt_group_cipher);wpa_sm_set_param(wpa_s->wpa, WPA_PARAM_MFP,}
еҲҶжһҗд»Јз ҒеҸҜзҹҘпјҢд№ҹе°ұжҳҜwpas_get_ssid_pmfиҝ”еӣһзҡ„з»“жһңдёҚдёҖж ·пјҢжҹҘзңӢwpas_get_ssid_pmfеҮҪж•°е®һзҺ°гҖӮ
int wpas_get_ssid_pmf(struct wpa_supplicant *wpa_s, struct wpa_ssid *ssid){if (ssid == NULL || ssid->ieee80211w == MGMT_FRAME_PROTECTION_DEFAULT) {if (wpa_s->conf->pmf == MGMT_FRAME_PROTECTION_OPTIONAL &&!(wpa_s->drv_enc & WPA_DRIVER_CAPA_ENC_BIP)) {/** Driver does not support BIP -- ignore pmf=1 default* since the connection with PMF would fail and the* configuration does not require PMF to be enabled.*/return NO_MGMT_FRAME_PROTECTION;}if (ssid &&(ssid->key_mgmt &~(WPA_KEY_MGMT_NONE | WPA_KEY_MGMT_WPS |WPA_KEY_MGMT_IEEE8021X_NO_WPA)) == 0) {/** Do not use the default PMF value for non-RSN networks* since PMF is available only with RSN and pmf=2* configuration would otherwise prevent connections to* all open networks.*/return NO_MGMT_FRAME_PROTECTION;}return wpa_s->conf->pmf;}return ssid->ieee80211w;В }
ж №жҚ®д»Јз ҒеҲҶжһҗпјҢе…¶еҹәжң¬зӯ–з•ҘеҰӮдёӢпјҡ
еҰӮжһңssid->ieee80211wдёҚзӯүдәҺй»ҳи®ӨеҖјпјҢеҚіMGMT_FRAME_PROTECTION_DEFAULTж—¶пјҢиҝ”еӣһssid->ieee80211wеҖјгҖӮ еҰӮжһңssid->ieee80211wзӯүдәҺй»ҳи®ӨеҖјж—¶пјҢйңҖиҰҒиҖғиҷ‘wpa_s->conf->pmfзҡ„жғ…еҶөгҖӮ еҰӮжһңwpa_s->conf->pmfдёәеҸҜйҖүпјҲеҚіMGMT_FRAME_PROTECTION_OPTIONALпјүпјҢдё”и®ҫеӨҮдёҚж”ҜжҢҒBIPеҠ еҜҶпјҲеҚідёҚж”ҜжҢҒmfpпјүпјҢеҲҷдёҚиө·з”ЁmfpеҠҹиғҪгҖӮ еҰӮжһңssid->key_mgmtеұһдәҺйқһRSNеҚҸи®®пјҢеҲҷдёҚиө·з”ЁmfpеҠҹиғҪгҖӮ еҗҰеҲҷпјҢиҝ”еӣһwpa_s->conf->pmfзҡ„еҖјгҖӮ
жүҖд»ҘпјҢжңҖз»Ҳи§ЈеҶіж–№жЎҲд№ҹе°ұеҮәжқҘдәҶпјҢеҸӘйңҖиҰҒеҰӮдёӢи®ҫзҪ®е°ұеҸҜд»ҘдәҶпјҡ
и®ҫзҪ®ssid->ieee80211w=MGMT_FRAME_PROTECTION_DEFAULTпјҢдҪҝз”Ёmfpзҡ„еҖјгҖӮ и®ҫзҪ®wpa_s->conf->pmf=MGMT_FRAME_PROTECTION_OPTIONALпјҢж №жҚ®и®ҫеӨҮжҳҜеҗҰж”ҜжҢҒmfpпјҢйҖүжӢ©жҖ§ејҖеҗҜmfpеҠҹиғҪгҖӮ
е…·дҪ“еҲ°й…ҚзҪ®е°ұжҳҜпјҡ
pmf=1 #йҖүжӢ©жҖ§ејҖеҗҜmfpеҠҹиғҪctrl_interface=/var/run/wpa_supplicantnetwork={ssid="your-ssid"key_mgmt=WPA-PSKpsk="your-psk"ieee80211w=3 # еҚіMGMT_FRAME_PROTECTION_DEFAULTпјҢеҸҜзјәзңҒscan_ssid=1}
OKпјҢ иҜҘй—®йўҳиҮіжӯӨеңҶж»Ўз»“жқҹпјҒ


